This was an interesting hardware challenge. I really enjoyed solving it. The method I used was to brute-force each pair of bytes. There might be another method to solve this challenge by studying the output and input results generated by the circuit and trying to find a pattern.
Challenge Description
The following pictures were given with the challenge:
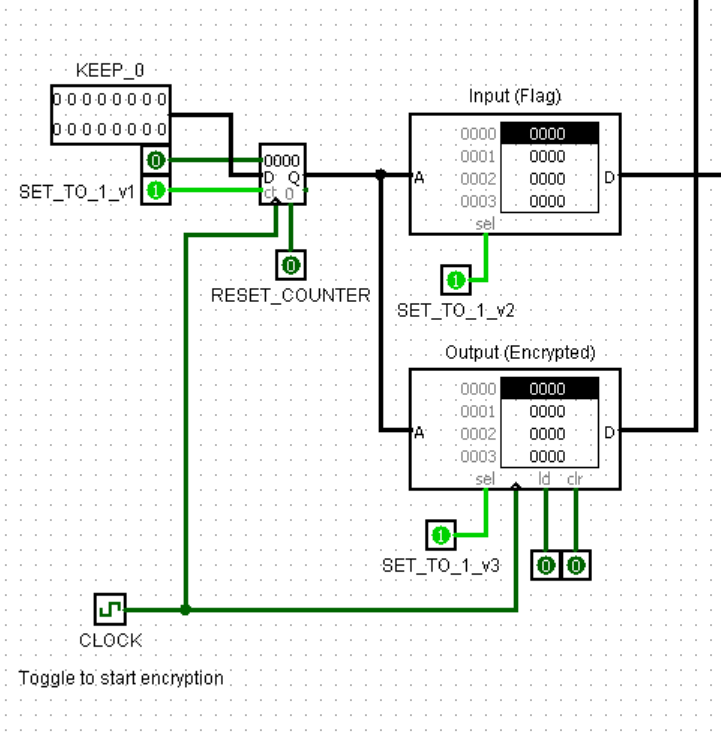
The flag was entered into the input, and its output was subsequently stored in the RAM, as depicted in the image below:
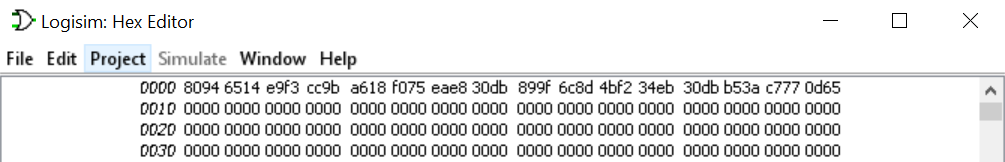
A file named RAM_output.txt was also given, here’s the content of it:
8094
6514
e9f3
cc9b
a618
f075
eae8
30db
899f
6c8d
4bf2
34eb
30db
b53a
c777
0d65
We were also given a logisim project that has the circuit, which will be helpful in understanding the circuit and in testing our solutions later on.
Analysis
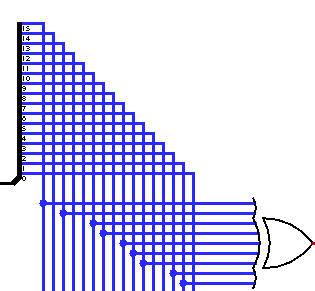
Analyzing the circuit, we can notice that each pair of bytes is XORed with random bits of each other. So there’s no particular key in this challenge; it just uses a basic algorithm to encode the flag by XORing each pair of bytes with each other’s bits. As shown in the pictures below, the two bytes are taken from the input, fed into the XOR ports, and the output of each XOR port is then taken and combined into two bytes that will be stored in the RAM.
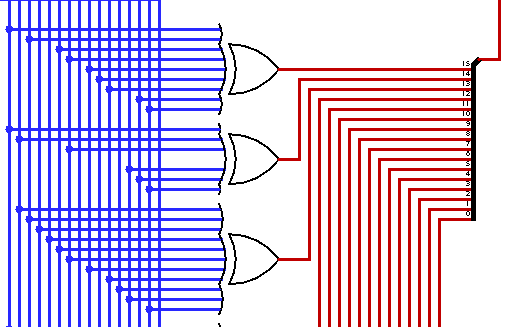
Solution
With the results of our analysis, we’ll need to replicate the circuit in a programmable manner so that we’ll be able to encode any two bytes of data the same way the circuit does. Since it’s only two bytes, I think brute-forcing our way will be faster than trying to reverse the full flag. So, let’s first create a multi-input XOR port that will XOR specific bits by given indexes.
def xor_bits(bits, indexes):
r = bits[indexes[0]]
for i in indexes[1:]:
r ^= bits[i]
return rNext up, using the full circuit as a reference (the picture below), I followed each connection of the 16 XOR ports and got the input indexes of each port to map them into the output.
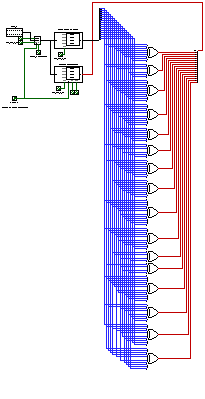
Using those mappings, I created the following function. It takes a bit vector as input and returns the value that the circuit would produce for the same bit vector.
def xor(bits):
output = [0] * 16
output[15] = xor_bits(bits, [15, 13, 10, 9, 7, 6, 5, 2, 1])
output[14] = xor_bits(bits, [15, 14, 9, 3, 2, 1])
output[13] = xor_bits(bits, [14, 13, 12, 11, 10, 9, 7, 5, 4, 3, 1])
output[12] = xor_bits(bits, [15, 14, 13, 12, 11, 8, 6, 5, 4, 3])
output[11] = xor_bits(bits, [12, 11, 10, 6, 5, 2, 1])
output[10] = xor_bits(bits, [15, 11, 9, 6, 3, 0])
output[9] = xor_bits(bits, [14, 10, 9, 8, 7, 5, 4, 1, 0])
output[8] = xor_bits(bits, [11, 10, 9, 8, 7, 6, 4, 2, 0])
output[7] = xor_bits(bits, [15, 14, 12, 11, 9, 8, 7, 6, 5, 4, 2, 0])
output[6] = xor_bits(bits, [15, 13, 12, 10, 9, 8, 6, 5, 1, 0])
output[5] = xor_bits(bits, [11, 10, 7, 2])
output[4] = xor_bits(bits, [14, 7, 6, 3])
output[3] = xor_bits(bits, [15, 14, 13, 12, 11, 10, 9, 8, 5, 4, 3, 0])
output[2] = xor_bits(bits, [15, 13, 7, 5, 3, 2, 1, 0])
output[1] = xor_bits(bits, [15, 14, 11, 9, 7, 6, 5, 4, 1, 0])
output[0] = xor_bits(bits, [14, 13, 12, 11, 9, 7, 5, 4, 3, 2])
return outputThis function, xor(bits), generates the output by XORing specific bits of the input bit vector according to the connections in the circuit. The helper function xor_bits(bits, indices) computes the XOR of bits at the specified indices in the input bit vector.
Here are two more functions that can assist with conversion: int2bits and bits2int.
def int2bits(n):
bits = bin(n).replace('0b', '')
if len(bits) < 16:
bits = ('0' * (16 - len(bits))) + bits
bits = bits[::-1]
bits = list(map(int, list(bits)))
return bits
def bits2int(bits):
rbits = bits[::-1]
rbits = list(map(str, rbits))
rbits = '0b' + ''.join(rbits)
return eval(rbits)The RAM output was given as text file with each line containing a word (2 bytes of data) represented in hex, I wrote a function to load them.
def load_data():
ram_output = open('RAM_output.txt')
data = ram_output.read()
ram_output.close()
words = []
for line in data.split("\n"):
if line:
words += [eval('0x' + line)]
return wordsAnd finally, here’s the brute-forcing part. As we know, the flag will be in ASCII characters, which means bytes from 0x20 to 0x7f. The script goes through all of the possible combinations, performs the XOR operation, and compares the result with the encoded value. If it is equal, then we have found the original word.
if __name__ == "__main__":
xored_words = load_data()
words = ''
for i in range(len(xored_words)):
xored_word = hex(xored_words[i]).replace('0x', '').rjust(4, '0')
for hn in range(0x20, 0x7f):
for ln in range(0x20, 0x7f):
v = (hn << 8) + ln
w = get_hex(v)
if (w == xored_word):
orw = hex(v).replace('0x', '')
print(xored_word, '->', orw)
words += orw
print("Flag: ", bytes.fromhex(words).decode())After running the script:
8094 -> 4c33
6514 -> 414b
e9f3 -> 7b58
cc9b -> 3052
a618 -> 5f31
f075 -> 735f
eae8 -> 4561
30db -> 5331
899f -> 6c59
6c8d -> 5f52
4bf2 -> 3376
34eb -> 4572
30db -> 5331
b53a -> 424c
c777 -> 6521
Flag: L3AK{X0R_1s_EaS1lY_R3vErS1BLe!
The flag was not complete for some reason. Looking at the RAM_output.txt file, we see that two bytes have not been decoded: 0d65. We know that the last byte is clearly } to conform to the flag format, but I just guessed on the byte 0d and tried !, and that was the correct flag: L3AK{X0R_1s_EaS1lY_R3vErS1BLe!!}.
Full Script
Here’s the full script:
def xor_bits(bits, indexes):
r = bits[indexes[0]]
for i in indexes[1:]:
r ^= bits[i]
return r
def int2bits(n):
bits = bin(n).replace('0b', '')
if len(bits) < 16:
bits = ('0' * (16 - len(bits))) + bits
bits = bits[::-1]
bits = list(map(int, list(bits)))
return bits
def bits2int(bits):
rbits = bits[::-1]
rbits = list(map(str, rbits))
rbits = '0b' + ''.join(rbits)
return eval(rbits)
def xor(bits):
output = [0] * 16
output[15] = xor_bits(bits, [15, 13, 10, 9, 7, 6, 5, 2, 1])
output[14] = xor_bits(bits, [15, 14, 9, 3, 2, 1])
output[13] = xor_bits(bits, [14, 13, 12, 11, 10, 9, 7, 5, 4, 3, 1])
output[12] = xor_bits(bits, [15, 14, 13, 12, 11, 8, 6, 5, 4, 3])
output[11] = xor_bits(bits, [12, 11, 10, 6, 5, 2, 1])
output[10] = xor_bits(bits, [15, 11, 9, 6, 3, 0])
output[9] = xor_bits(bits, [14, 10, 9, 8, 7, 5, 4, 1, 0])
output[8] = xor_bits(bits, [11, 10, 9, 8, 7, 6, 4, 2, 0])
output[7] = xor_bits(bits, [15, 14, 12, 11, 9, 8, 7, 6, 5, 4, 2, 0])
output[6] = xor_bits(bits, [15, 13, 12, 10, 9, 8, 6, 5, 1, 0])
output[5] = xor_bits(bits, [11, 10, 7, 2])
output[4] = xor_bits(bits, [14, 7, 6, 3])
output[3] = xor_bits(bits, [15, 14, 13, 12, 11, 10, 9, 8, 5, 4, 3, 0])
output[2] = xor_bits(bits, [15, 13, 7, 5, 3, 2, 1, 0])
output[1] = xor_bits(bits, [15, 14, 11, 9, 7, 6, 5, 4, 1, 0])
output[0] = xor_bits(bits, [14, 13, 12, 11, 9, 7, 5, 4, 3, 2])
return output
def get_hex(v):
bits = int2bits(v)
xored_bits = xor(bits)
rint = bits2int(xored_bits)
return hex(rint).replace('0x', '')
def load_data():
ram_output = open('RAM_output.txt')
data = ram_output.read()
ram_output.close()
words = []
for line in data.split("\n"):
if line:
words += [eval('0x' + line)]
return words
if __name__ == "__main__":
xored_words = load_data()
words = ''
for i in range(len(xored_words)):
xored_word = hex(xored_words[i]).replace('0x', '').rjust(4, '0')
for hn in range(0x20, 0x7f):
for ln in range(0x20, 0x7f):
v = (hn << 8) + ln
w = get_hex(v)
if (w == xored_word):
orw = hex(v).replace('0x', '')
print(xored_word, '->', orw)
words += orw
print("Flag: ", bytes.fromhex(words).decode())